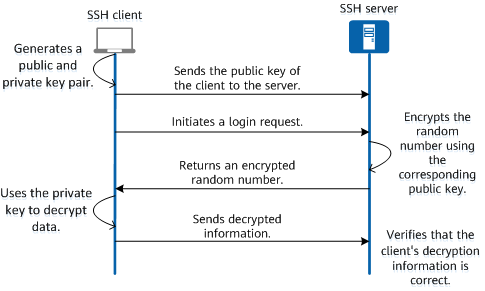
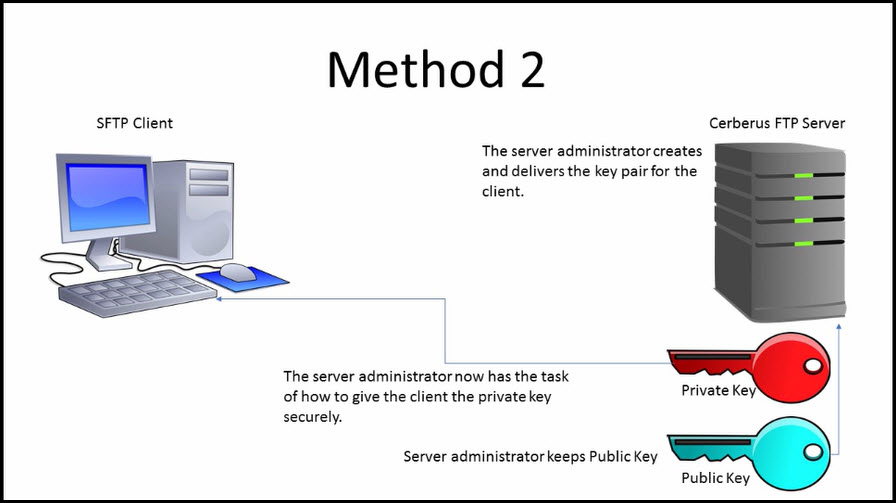
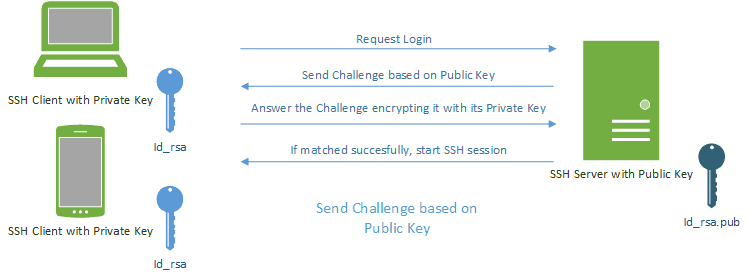
How to setup SSH key based authentication on Linux server - Reference Server - DYclassroom | Have fun learning :-)
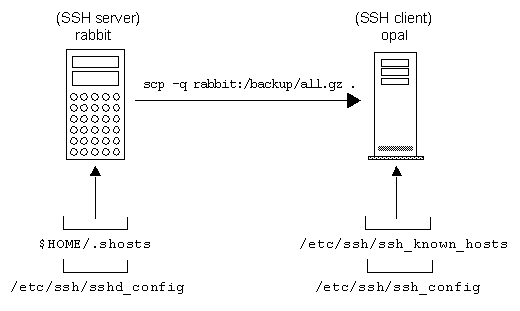
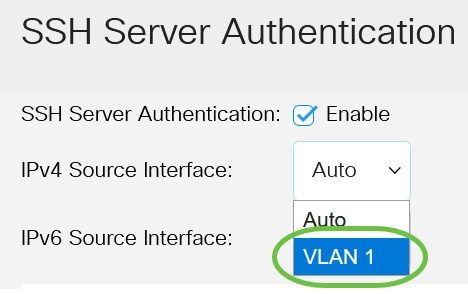
SSH connection setting method for Windows (when the PFM - RM host is running Windows and the monitored host is running UNIX)

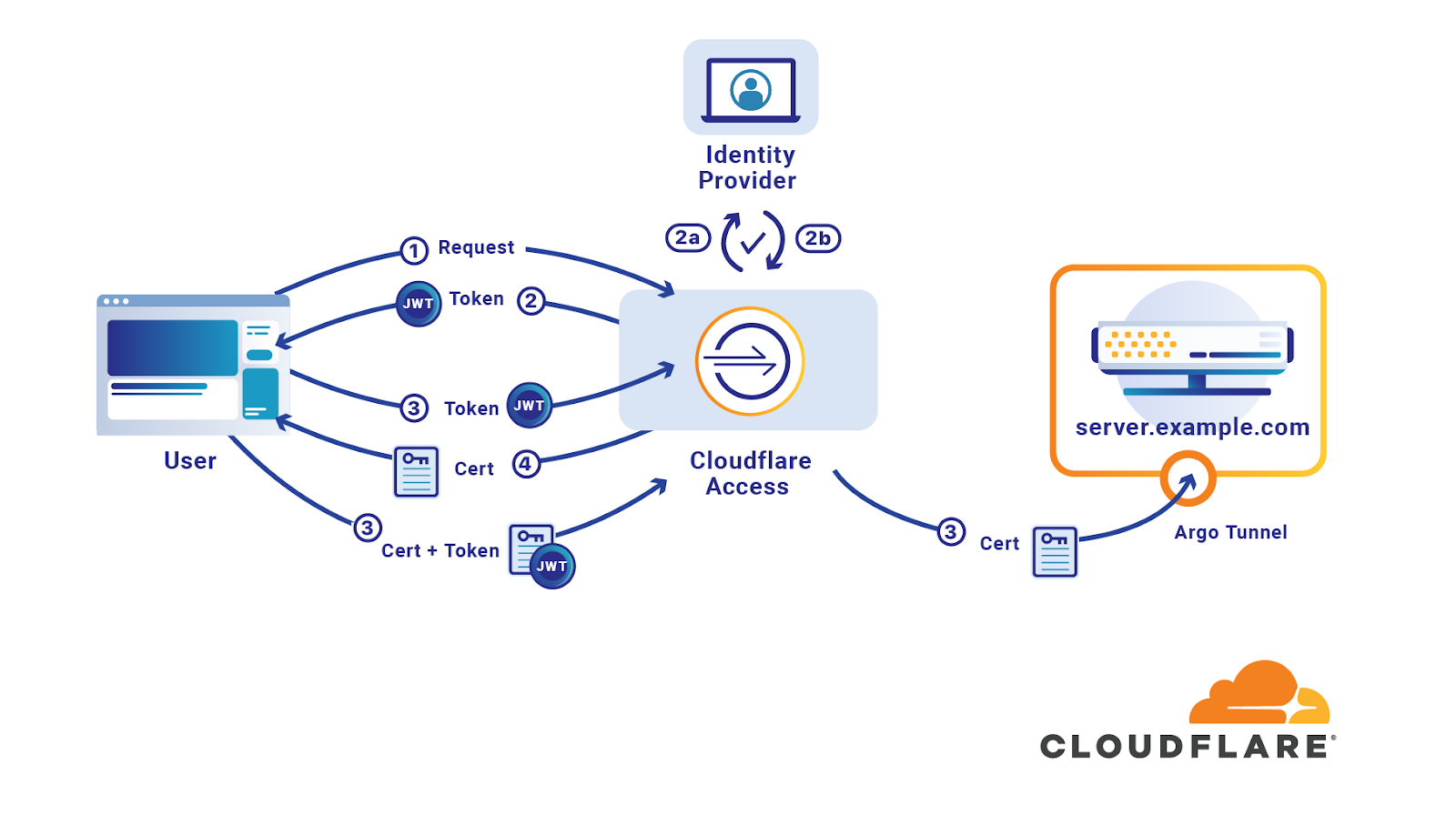
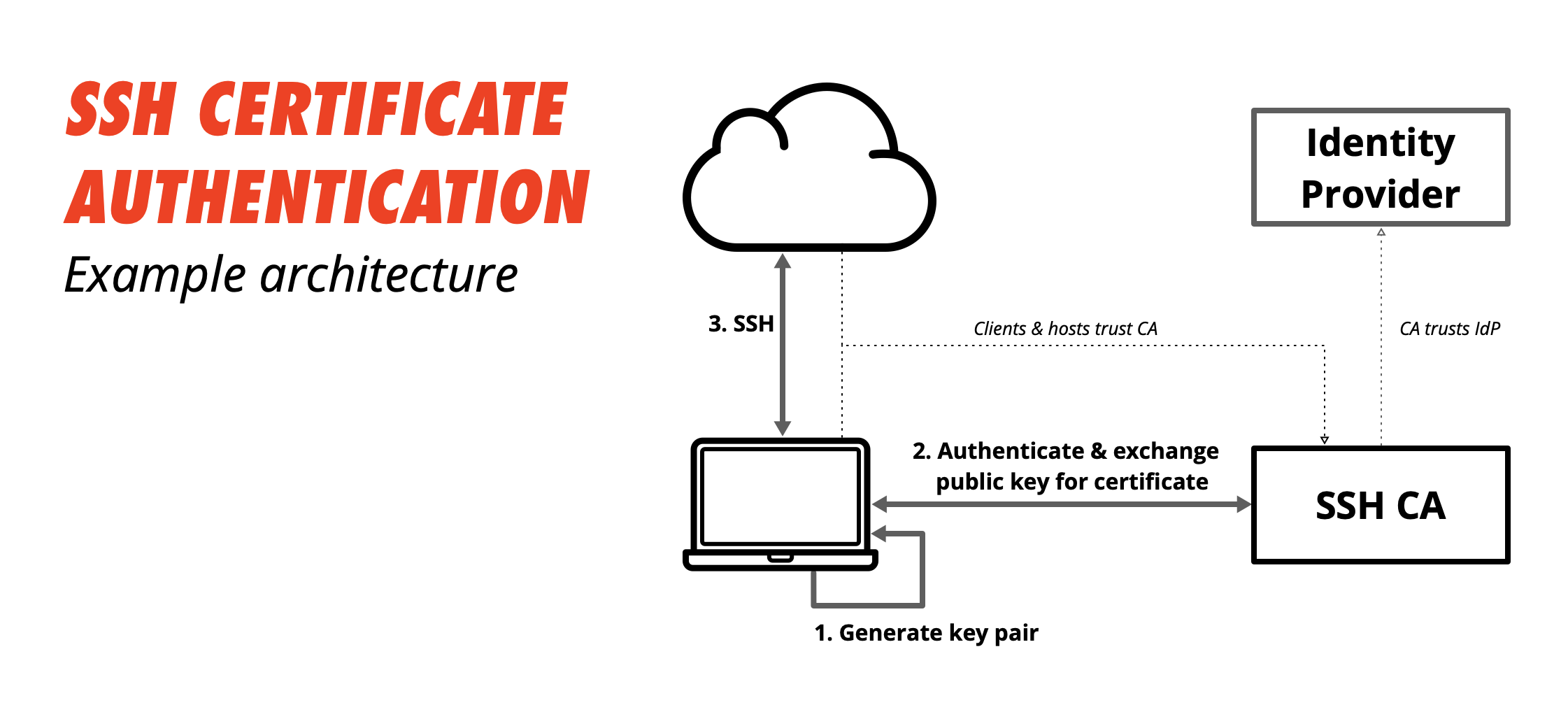
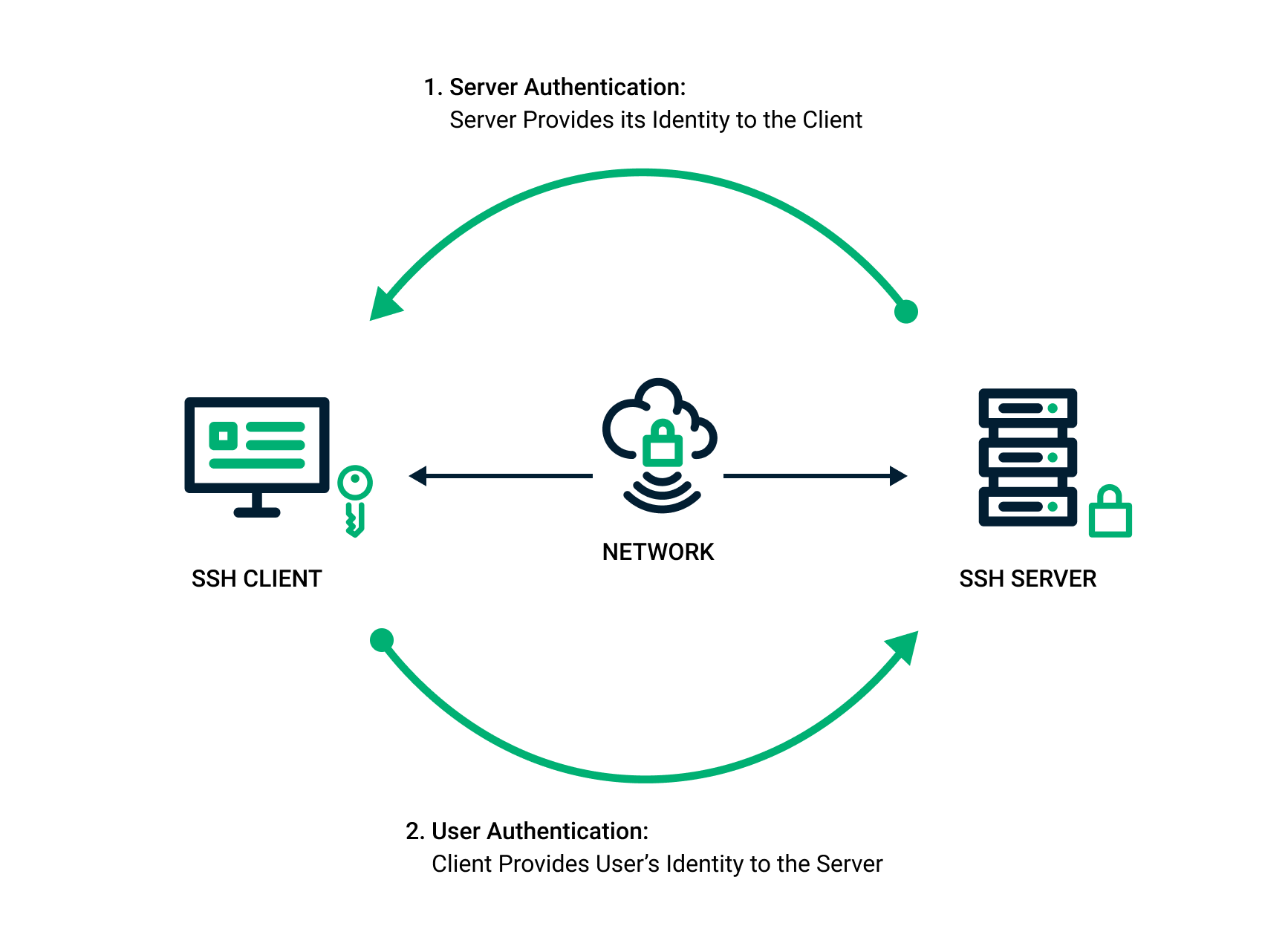
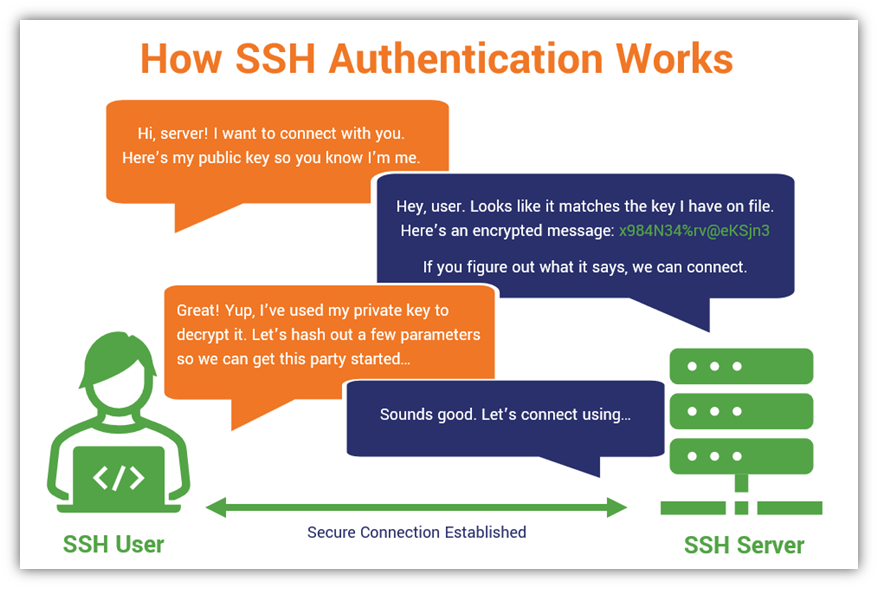
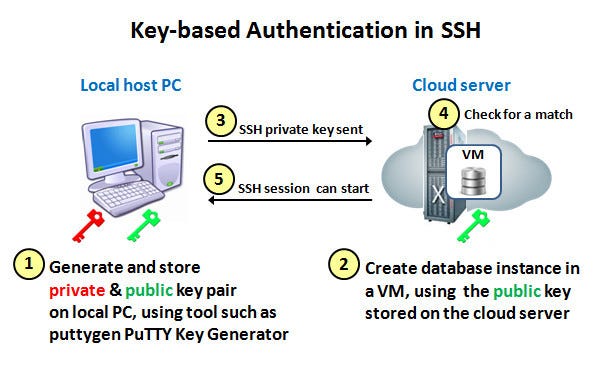
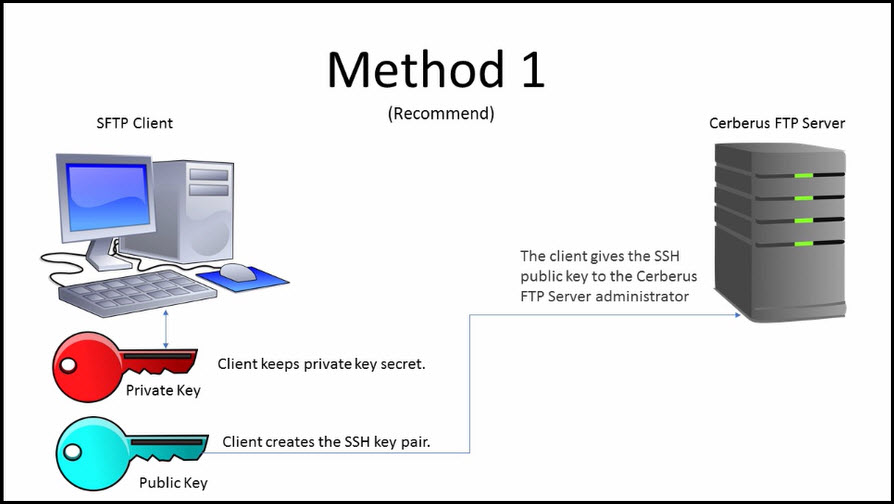
SSH keys authenticate users and hosts in SSH. They are used for single sign-on and machine-to-machine access. Security and convenience!